FMS President Luke Chung attended the 2019 Portland Access User Group Conference in Silver Falls, Oregon. While there, Luke explored the beautiful Silver Falls State Park with fellow Microsoft Access Developers. Here are some of the breath taking photos. For more information on the PAUG 2019 conference, visit the Portland Access User Group site.
Category Archives: Microsoft Access
2019 Netherlands Access Developer Day
Here are some photos from the 2019 Netherlands Access Developer Day Conference. FMS President Luke Chung gave a presentation on the Microsoft Access Database Evolution from the Desktop to the Cloud. For more information on the NADD 2019 conference, visit Netherlands Access Developer Day.
Total Access Analyzer Update for 2019, 2016, 2013, 2010 and 2007
Total Access Analyzer examines all your database objects to provide extensive documentation, code analysis, object cross-reference, and diagrams with over 430 presentation-quality reports.It detects 430+ types of errors, suggestions, and performance tips, so you can learn and apply Best Practices to fix problems, improve your design, and speed up your Access applications.
Enhancements:
- Ribbon Documentation
- Data Macro Analysis
- SQL Cross-Reference and Validation of Subform References
- New Errors and Suggestions
- Report Enhancements
- View Explorer Enhancements
- Quick Documentation Enhancements
- About Box has Check for Updates
- Improved User Interface
- Revised User Manual and Help File
- and more…
For more information, visit:
- Total Access Analyzer 2019, Version 17.1
- Total Access Analyzer 2016, Version 16.7
- Total Access Analyzer 2013, Version 15.7
- Total Access Analyzer 2010, Version 14.7
- Total Access Analyzer 2007, Version 12.97
Existing Total Access Analyzer owners are able to upgrade at a discounted price.
Use Microsoft SQL Server Database Users Rather than Server Logins
 FMS President Luke Chung wrote a new paper on improving Microsoft SQL Server security by using database users rather than server logins:
FMS President Luke Chung wrote a new paper on improving Microsoft SQL Server security by using database users rather than server logins:
Microsoft SQL Server Database Users and Permissions Instead of Server Logins.
Here’s an overview:
 Microsoft SQL Server Security Logins Introduction
Microsoft SQL Server Security Logins Introduction
To connect to a Microsoft SQL Server database, it requires a login which includes a user name and password. Each database server has a login with administrator permissions that allows the creation and deletion of databases.
Often, this login is distributed which creates a security problem. Developers and end-users shouldn’t have administrator permissions to perform their tasks. Their permissions should be managed for each database.
Database User Permissions
Microsoft SQL Server makes it easy to create and manage database permissions. The permissions you grant are called roles and users are able to have multiple roles. Here are some examples of the permissions you are able to assign to users.
Full Database Permissions (Owner)
This allows the database developer full rights to make modifications to the database objects.
Editing Permissions (Writer)
End-users who need to add, delete and change data in user tables.
Read Only Permissions (Reader)
Only allows the end-user to view data in the user tables.
Read our Microsoft SQL Server Users and Permissions paper for more information on how to do this and some pitfalls to avoid. It applies to SQL Server whether it’s installed on premise or in the Azure cloud.
Government Shutdown’s Impact on Contractors and Employees
Contractors Face Considerable Financial Risk
With Congress and President Trump at a budget impasse, funding for significant portions of the US Federal government ended midnight Friday, December 18, 2018. Historically, government employees are not paid on time but are retroactively paid after the new budget is implemented. The same is not true for government contractors.
Government contractors compete against each other to provide a wide range of services such as computer programming, construction, security guards, cafeterias, janitorial services, technical experts, maintenance workers, and much more. When the government shuts down, contractor staff are not needed or can’t do their work. But they are real companies and people who suffer. Long-term, it’s bad for US taxpayers.
Our Contract with Amtrak is Suspended
We have a government contract with Amtrak which was suspended by this letter:

This contract provides help for Microsoft Access database programming and is relatively small. We do not have dedicated staff for the contract, so we are not really affected as our people will work on other projects.
Unfortunately, we have colleagues who are government contractors or in businesses more dependent on the government who are significantly impacted by the shutdown. This is especially true for companies who provide staff to work at government facilities that are now closed. Most are hesitant to speak publicly about their experiences in fear their government clients would be offended, so we’d like to share our experiences and theirs.
Very Tough Situation and Decisions for Government Contractors and Their Employees
Since government contractors are unlikely to be repaid when the budget is finally resolved, government contractors with dedicated staff for those contracts need to decide whether to pay their employees for time they never expected to not charge to the government. The impact is somewhat offset by the Christmas and New Year’s holidays, and maybe they can force employees to take vacation days. But as the shutdown lasts longer, contractors will have to pay their employees from their own funds. Not paying them runs the risk that the employees leave and won’t be available once the budget is resolved. One cannot expect employees to remain loyal if they aren’t paid. Meanwhile, employees are dusting off their resumes and seeking alternative employers.
Small businesses are especially vulnerable since many contracts have small profit margins, so without significant cash and lines of credit, a cash flow problem can quickly bankrupt a company. Even generous owners who try to do the “right thing”, may not be able to if their cash is depleted. That would lead to fewer government contractors in the future and higher costs to taxpayers.
A friend of mind who owns a firm completely focused on servicing the federal government shared:
“As contractors, our employees still get paid and yet we are unable to bill. Cash is king and small companies like mine live and die by cash. This is the worst.”
Media Coverage
On December 26th, we sent a Twitter message with the letter we received from Amtrak and the sympathy we feel for government contractors and their employees.
![]() That led to our inclusion in a Washington DC News article on WUSA Channel 9 (CBS) by John Henry that evening. A video of the coverage with our Amtrak letter and insight are in this article: #ShutdownStories: Government contractors tackle life without pay during partial shutdown
That led to our inclusion in a Washington DC News article on WUSA Channel 9 (CBS) by John Henry that evening. A video of the coverage with our Amtrak letter and insight are in this article: #ShutdownStories: Government contractors tackle life without pay during partial shutdown
![]() On December 27th, I was interviewed in the Huffington Post article by Sarah Ruiz-Grossman about the challenges facing contractors entitled
On December 27th, I was interviewed in the Huffington Post article by Sarah Ruiz-Grossman about the challenges facing contractors entitled
Shutdown Leaves Government Contractors Without Work And Likely No Back Pay.
“Business owners who have [dedicated] staff are making the decision: Do we pay people or not, even though we won’t get paid by the government? Either you force people to take vacation, or you pay them, to be a good company ― but depending how long it drags on, one may not have a choice.”
![]() On December 27th, Bridget Johnson included us in her Homeland Security Today article:
On December 27th, Bridget Johnson included us in her Homeland Security Today article:
Federal Employees, Contractors Tweet Worries with #ShutdownStories
Self-Inflicted Wound that Should be Resolved Promptly
Eventually the budget will be resolved. We hope the parties come to their senses and do it sooner rather than later because innocent people who’ve dedicated their firms and lives to providing a professional service to US taxpayers are at risk and feeling real pain. That’s terrible for them now and our country long-term.
Microsoft Azure Security Holes with SQL Server Databases
 FMS President Luke Chung wrote a new paper to deal with Microsoft Azure Security Holes with SQL Server Databases
FMS President Luke Chung wrote a new paper to deal with Microsoft Azure Security Holes with SQL Server Databases
Here’s an overview:
 Microsoft SQL Azure Security Introduction
Microsoft SQL Azure Security Introduction
Having Microsoft Azure host SQL Server databases on their servers is very cost-effective and efficient. Within minutes, one can have a SQL Server database hosted in the cloud and available to applications on the cloud or on premise.
As with all cloud resources, and especially databases, security is a huge concern. Fortunately, SQL Azure includes features to restrict what can connect to your database server but you need to know how to use them and realize that the default settings do not protect you best.
Setting Firewalls and Virtual Networks
This is an important feature for cloud solutions so that only permitted sources are allowed to get data from your server and databases. You can set the IP Addresses you allow at the database level and server level. The database settings take precedence over the server settings.
Cannot Open Server Error
If you try to connect to the database from an unauthorized IP address, it triggers an error like this:
Cannot open server ‘ServerName’ requested by the login. Client with IP address ‘111.222.33.44’. is not allowed to access the server. To enable access, use the Windows Azure Management Portal or run sp_set_firewall_rule on the master database to create a firewall rule for this IP address or address range. It may take up to five minutes for this change to take effect.
By Default, All Azure Resources can Connect to Your Database
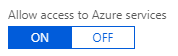
By default, all Azure resources can connect to your server and databases hosted on Azure:
Allowing All Azure Services to Connect to Your Server is a Huge Security Hole!
If you “Allow access to Azure Services” set to On, you create a huge security hole for your server and every database in it. Not only can all your resources connect to your databases, Any Azure resource from any organization can connect to your database.
This setting is NOT restricted to the Azure resources in your subscription. It’d be nice to restrict permissions to the current subscription or list of subscriptions but that’s not possible. It’s everything on all of Microsoft Azure or you need to specify each IP address.
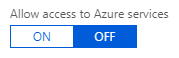
Turn Off Permissions to All Azure Services
Set the permissions to OFF to disallow all Azure services to connect to your SQL server:
Explicitly Specify the IP Addresses Allowed
To avoid the ability of rogue Azure resources from breaching your database security, you need to manually specify the IP Address of every resource that may connect to your server and databases. This can be a real pain.
For more details and how to set your IP Addresses and SQL Azure security correctly, read our new paper: Microsoft Azure Security Holes with SQL Server Databases
Total Access Analyzer 2019 is Shipping
We are excited to announce the release of Total Access Analyzer for Microsoft Access 2019! Total Access Analyzer examines all your database objects to provide extensive documentation, code analysis, object cross-reference, and diagrams with over 390 presentation-quality reports.It detects 300+ types of errors, suggestions, and performance tips, so you can learn and apply Best Practices to fix problems, improve your design, and speed up your Access applications.>New Features
Access Analyzer 2019 is an upgrade from the 2016 version and includes these enhancements:
 Supports Microsoft Access 2019, 32-bit and 64-bit versions.
Supports Microsoft Access 2019, 32-bit and 64-bit versions.- Document All Database types supported by Microsoft Access 2019.
- Improved Blueprint Documentation.
- Additional Cross-Reference and Validation including Subform References.
- Improved Memory Management.
- Data Macro Documentation.
- Document Workgroup Security in ACCDBs.
- Better Support of Documentation for Multiple Databases.
- Module Bracket Reports.
- Improved User Interface Shows more Progress Details.
- New Manual and Context Sensitive Help.
- and more…
Existing Total Access Analyzer owners are able to upgrade at a discounted price.
New updates for Total Access Analyzer 2016, 2013, 2010 and 2007
Enhancements
- Additional Cross-Reference and validation of tables, queries, fields and controls across your database objects, including references in subforms.
- Improved form and report blueprint documentation to capture large and complicated designs and layouts.
- Improved memory management for documenting large Access databases to minimize the chance of running out of memory.
- Data macro documentation and cross references to related tables.
- Documentation of workgroup security settings for ACCDBs if they wer converted from MDBs with workgroup security.
- Improved user interface to show progress of the documentation.
- Revised user manual and help file.
- and more…
For more information, visit:
- Total Access Analyzer 2016 Build: 16.10.0040
- Total Access Analyzer 2013 Build: 15.60.0040
- Total Access Analyzer 2010 Build: 14.60.0040
- Total Access Analyzer 2007 Build: 12.96.0040
Download the Free Trial to experience it for yourself.
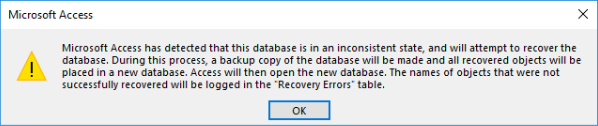
Microsoft Access has detected that this database is in an inconsistent state
Recently, Microsoft Access users are confronted with this error when they open their database on Windows 10 machines:
“Microsoft Access has detected that this database is in an inconsistent state, and will attempt to recover the database. During this process, a backup copy of the database will be made and all recovered objects will be placed in a new database. Access will then open the new database. The names of objects that were not successfully recovered will be logged in the ‘Recovery Errors’ table.”
This seems to be related to Microsoft security updates that were released over the past few months.Our investigations lead us to these two links:
Microsoft Explanation
Microsoft discusses this problem here: Microsoft Access reports that databases are in an ‘inconsistent state’
Workaround
A potential workaround suggests to ensure that SMBv2 or SMBv3 is enabled on both client and server, as described in this Knowledge Base article:
How to detect, enable and disable SMBv1, SMBv2, and SMBv3 in Windows and Windows Server
We hope you find this helpful. Let us know your experience with this.
Total Access Emailer Update for Microsoft Access 2016
Total Access Emailer is the most popular email automation system for Microsoft Access. A new update was released for the Microsoft Access 2016 version.
Enhancements
- Partially Restored Original SMTP ValidationTechnique.
- Validation of FROM Address during Email Blasts.
- Adjusted the saving of datasheet column settings on databases before Access 2007.
- Improved Offline activation and uninstall.
- Cosmetic changes to the program and sample databases.
For more information, visit:
- Access 2016 Build: 16.01.0016
Existing Total Access Emailer 2016 owners were notified to download the update.
Total Access Emailer Update for Microsoft Access 2016
Total Access Emailer is the most popular email automation system for Microsoft Access. Update 16.01.0014 was released for the Microsoft Access 2016 version.
Enhancements
- SMTP validation uses your email address and eliminates the need to use a TEmail.txt file.
- Changes you make in the datasheets settings such as column settings, sort order, and/or filters are saved where appropriate for the next time the form is opened.
- Preview Text allows you to test your email blasts by sending the emails to your own email address.
- When creating an email blast, the FROM email address is validated for an acceptable email format.
- When the name of an attachment file includes invalid characters (e.g. :*?”<>|), a message indicates that problem rather than saying the file can’t be found.
- Procedure TotalAccessEmailer_SendOne has two parameters (strMessageHTML and strHTMLFile) that are optional but were previously required.
- Sample database updated with TLS option and larger fonts.
- Cosmetic changes to increase font size, widen combo boxes, font consistency, and support for higher resolution monitors.
- Manual and help file updated.
The latest update for Total Access Emailer 2016, Version 16.0 is:
- Access 2016 Build: 16.01.0016
Existing Total Access Emailer 2016 owners were notified to download the update.