 FMS President Luke Chung wrote a new paper to deal with Microsoft Azure Security Holes with SQL Server Databases
FMS President Luke Chung wrote a new paper to deal with Microsoft Azure Security Holes with SQL Server Databases
Here’s an overview:
 Microsoft SQL Azure Security Introduction
Microsoft SQL Azure Security Introduction
Having Microsoft Azure host SQL Server databases on their servers is very cost-effective and efficient. Within minutes, one can have a SQL Server database hosted in the cloud and available to applications on the cloud or on premise.
As with all cloud resources, and especially databases, security is a huge concern. Fortunately, SQL Azure includes features to restrict what can connect to your database server but you need to know how to use them and realize that the default settings do not protect you best.
Setting Firewalls and Virtual Networks
This is an important feature for cloud solutions so that only permitted sources are allowed to get data from your server and databases. You can set the IP Addresses you allow at the database level and server level. The database settings take precedence over the server settings.
Cannot Open Server Error
If you try to connect to the database from an unauthorized IP address, it triggers an error like this:
Cannot open server ‘ServerName’ requested by the login. Client with IP address ‘111.222.33.44’. is not allowed to access the server. To enable access, use the Windows Azure Management Portal or run sp_set_firewall_rule on the master database to create a firewall rule for this IP address or address range. It may take up to five minutes for this change to take effect.
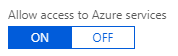
By Default, All Azure Resources can Connect to Your Database
By default, all Azure resources can connect to your server and databases hosted on Azure:
Allowing All Azure Services to Connect to Your Server is a Huge Security Hole!
If you “Allow access to Azure Services” set to On, you create a huge security hole for your server and every database in it. Not only can all your resources connect to your databases, Any Azure resource from any organization can connect to your database.
This setting is NOT restricted to the Azure resources in your subscription. It’d be nice to restrict permissions to the current subscription or list of subscriptions but that’s not possible. It’s everything on all of Microsoft Azure or you need to specify each IP address.
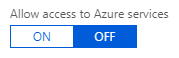
Turn Off Permissions to All Azure Services
Set the permissions to OFF to disallow all Azure services to connect to your SQL server:
Explicitly Specify the IP Addresses Allowed
To avoid the ability of rogue Azure resources from breaching your database security, you need to manually specify the IP Address of every resource that may connect to your server and databases. This can be a real pain.
For more details and how to set your IP Addresses and SQL Azure security correctly, read our new paper: Microsoft Azure Security Holes with SQL Server Databases
Leave a Reply